Setting Up a LAN With Multiple Gateway/interface With Iptables and Route Policy Under Awesome Linux by sunus Lee is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 3.0 Unported License.
Introduction
First of all, it all because my MacBookPro’s xl2tp utils can not work under my school’s networking enviroment. so this is how the post is born.
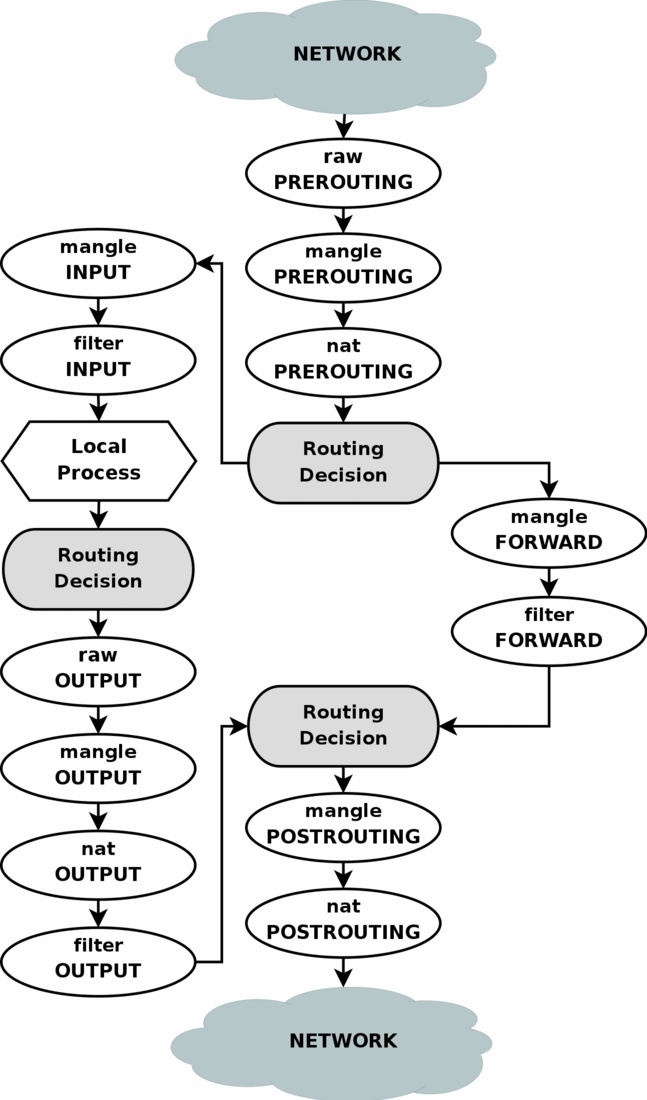
I have been digging with those stuffs for almost a week, and now, finally i get it rolling and it seems awesome. this post will talks about netfilter known as iptables and ip route policy. and some technic/tool like tcpdump will be involved as well.
Environment
The environment i have is like this below:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| ----------------- -----------------
| Slow | | Fast |
| Internet-1 | | Internet-2 |
| 10.10.149.1 | | 123.150.232.1 |
----------------- -----------------
| |
[eth0.2] | |[ppp0]
| |
--------------------------
| Route, Running Linux |
| br-lan: 192.168.1.1 | [br-lan] ------------------------
| ppp0: 123.150.232.74 | --------------| Other Machines in Lan|
| eth0.2: 10.10.149.4 | ------------------------
--------------------------
| |
[br-lan]| |[br-lan]
| |
| |
| |
------------------------- ----------------------
|ArchLinux | | MacBook |
|eth0: 192.168.1.245 | | en0:192.168.1.169 |
|ppp0: 180.134.135.173 | | |
------------------------- ----------------------
|
|
|
|
------------------
| Fast |
| Internet-3 |
| 180.134.135.1 |
------------------
|
after connect the wires. there is three ** physic wires **:
- Route <——> **Slow Internet-1 **this is the only one that connects to outside my dorm. via route’s port WAN.
- Route <——> ** ArchLinux ** this one is in a Route’s port #1 LAN
- Route <——> ** MacBook ** same as above, using Route’s port #2 LAN
There is also something to be noticed:
-
the ppp0 in Route is a high-speed connection(VPN). it needs to go though eth0.2 to connect the VPN-server, then it will generate a Virtual Network InterFace, that is, ppp0.
-
the another ppp0 in ArchLinux is also the high-speed connection. but firstly, it goes to Route, then the VPN-server.
-
in this environment, you can consider those ppp0 as real NICs that are connected to the internet as well.
-
So, we can say eth0.2 and two ppp0 are all outgoing Interfaces.
Solutions
-
I repeat what i want to accomplished here:
1 . i want my MacBook can connected to the internet.
2 . i want my MacBook’s internet connection to be as FAST as possible.
-
Before we get started, there’s something we can do and can’t do, in general.
1 . Seting the default route to 180.134.135.1 for ArchLinux and a route to lan. We do this because we want all the trafftic goes to a fast internet connecting while we keep the connection to the other machines in the lan still work.
# route add -net 192.168.1.0/24 gw 192.168.1.1 dev eth0
# route add default gw 180.134.135.1 dev ppp0
2 . Because there is other machines in the lan, so we can not set 123.150.232.1 as default route for Route, just like the ArchLinux. there is only ** me ** can access the Fast Internet-2.( The Benefit of being me or with me :) lol! )
The Slow Solution
-
Making the MacBook can connect to the internet, but it just too slow for me. Just set up machines and route like the diagram above, it will result this:
1 . the ArchLinux using Internet-3.
2 . the MacBookPro using Slow-Internet-1
The A Little Bit Faster Solution
- Making the MacBook Using ArchLinux’s Internet-3 and the ArchLinux still keep unchanged in Slow Solution. This solution requires those steps.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| * in the MacBook, change default route from 192.168.1.1 to 192.168.1.245
In MacBook:
# route add default 192.168.1.245
# route del default 192.168.1.1
* in ArchLinux, set up a route policy/rule
* the packets that comes from MacBook(192.168.1.169), Using the gateway of Internet-3.
In ArchLinux:
# add a empty table to route table
echo '7375 SunusRules' >> /etc/iproute2/rt_tables
# add a default route rule to newly create table SunusRules
ip route add default via 180.134.135.173 dev ppp0 table SunusRules
# add this table to routing rules, all the packet comes from MacBook, apply this route rule.
ip rule add from 192.168.1.169 table SunusRules
* We are done here.
* In fact, i don't think add a route rule here is necessarily, but anyway, it's a good time to get the first impression of what this can do. which we will make the best use of it in next Solution.
|
The Ultimate And More Fast Solution, so far
More useful resources.
##i read a lot of them to make this work, i think you should do that, too. if you relly want to fully utilize your network.
- the iptable-tutorial
- the awesome and notable Linux Advanced Routing & Traffic Control, aka ‘lartc’
-
much more you will find in those two above.
- 1,2 also have Chinese version, thank for those guy who do the translation work!
PS
since i now got kinda experience of doing those stuffs, you are welcome to leave a message or just email me about what you think or what you want to do. i will try to help you if i can.
ANY questions and discussion are welcomed, too.